If we look at business software (custom made or off the shelf), most of them rely of feedback mechanism but feedback mechanism is built into the process which is largely human driven not on the automatic path. This thought makes any process human intensive and resource hungry.
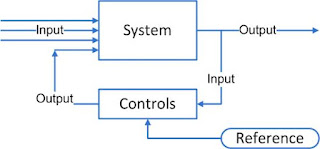
Any process can be represented as
In this system it has been assumed that system is perfect, input received by system are perfect and comply to specifications ( zero tolerance), System is perfect (Zero tolerance) and always work as though of ( not only as designed). But we do not live in utopia.
To accommodate imperfect world, feedback based systems are used.
Feedback systems are basis of control engineering.
Control engineering basic foundation can be summarized as:
1. A system that has no corrective feedback is likely to diverge from the desired output.
2. A system that tries to correct too quickly will likely overrun the mark and oscillate around the desired value.
3. A system that corrects too slowly will take a long time to reach the desired value, if it ever does.
4. A system with delayed corrective feedback will generally oscillate at a frequency related to the delay time.
From system thinking perspective, where cause and effect loop into feedback system, one can think of:
1. Stabilizing Loop: It leads to a balance. The more food I eat, and then the fuller I feel. The fuller I feel then the less food I eat.
2. Reinforcing Loop. This loop continues till some external agent intervenes. The more I think of food then the hungrier I get and the hungrier I get then the more I think of food.
3. Choice: This is not about loop but making a choice. Our machines are not intelligent (sic!) enough to make choice, so human (or living being) are invariably get involved in these type of system. I think about food and make a choice to eat food. Choice may lead to increase or decrease in effect.
4. Choice and Reinforcing Feedback: In some cases choice and reinforcing feedback combine and create an addictive effect. I think about money, I earn more money. I think more about money.
References:
1. http://www.developerdotstar.com/mag/articles/gray_diagram_of_effects.html
2. Quality Software Management, Vol 1: Systems Thinking by Gerald M. Weinberg
3. The Fifth Discipline: The Art & Practice of The Learning Organization by Peter M. Senge
Any process can be represented as
In this system it has been assumed that system is perfect, input received by system are perfect and comply to specifications ( zero tolerance), System is perfect (Zero tolerance) and always work as though of ( not only as designed). But we do not live in utopia.
To accommodate imperfect world, feedback based systems are used.
Feedback systems are basis of control engineering.
Control engineering basic foundation can be summarized as:
1. A system that has no corrective feedback is likely to diverge from the desired output.
2. A system that tries to correct too quickly will likely overrun the mark and oscillate around the desired value.
3. A system that corrects too slowly will take a long time to reach the desired value, if it ever does.
4. A system with delayed corrective feedback will generally oscillate at a frequency related to the delay time.
From system thinking perspective, where cause and effect loop into feedback system, one can think of:
1. Stabilizing Loop: It leads to a balance. The more food I eat, and then the fuller I feel. The fuller I feel then the less food I eat.
2. Reinforcing Loop. This loop continues till some external agent intervenes. The more I think of food then the hungrier I get and the hungrier I get then the more I think of food.
3. Choice: This is not about loop but making a choice. Our machines are not intelligent (sic!) enough to make choice, so human (or living being) are invariably get involved in these type of system. I think about food and make a choice to eat food. Choice may lead to increase or decrease in effect.
4. Choice and Reinforcing Feedback: In some cases choice and reinforcing feedback combine and create an addictive effect. I think about money, I earn more money. I think more about money.
The clouds represent observable (and potentially measurable) quantities. A plain arrow indicates that an increase or decrease of one quantity influences a similar increase or decrease of the other.
If there is a dot on the arrow, then the effect is the opposite—an increase of one influences a decrease of the other.
With all of SOA and BPM why we are not able to deploy Stabilizing and Reinforcing Loop mechanisms in business software?
References:
1. http://www.developerdotstar.com/mag/articles/gray_diagram_of_effects.html
2. Quality Software Management, Vol 1: Systems Thinking by Gerald M. Weinberg
3. The Fifth Discipline: The Art & Practice of The Learning Organization by Peter M. Senge