Thursday, June 17, 2010
Tuesday, June 15, 2010
Book Review: Cloud Computing – Implementation, Management and Security
Book Review: Cloud Computing – Implementation, Management and Security by John W. Rittinghouse and James F. Ransome: Publisher- CRC Press: ISBN- 13: 978-1-4398-0680-7
This is one book on cloud computing. From the topic it seems that book is targeted at the cloud provider community but it looses focus very often. Nevertheless it tries to provide other side of story which no other book in market is providing.
Book consists of nine chapters which covers history of computers, various services offered by cloud, introduction to virtualization, standards in cloud, some talk about security and privacy in cloud, and accessing the cloud. Book also have two appendices which covers hands on Sun VirtualBox and case study on executive talk on cloud adoption.
Book provide lot of references which I like particularly. Book also scratches few of the topic which no other book has covered ( at least I have not encountered) like security and privacy in cloud in detail ( there is scope of much improvement), identity management in cloud ( again with huge scope of improvement) etc.
I suggest, read this book once but certainly it does not deserve to be in my bookshelf.
Disclaimer: I did not get paid to review this book, and I do not stand to gain anything if you buy the book. I have no relationship with the publisher or the author.
One can get more information about book and related topics from:
1. Amazon: http://www.amazon.com/Cloud-Computing-Implementation-Management-Security/dp/1439806802
2. Flipkart: http://www.flipkart.com/cloud-computing-john-rittinghouse-james-book-1439806802
3. Dr. John W. Rittinghouse resume: http://www.aphanes.net/JR%20Bio.html
This is one book on cloud computing. From the topic it seems that book is targeted at the cloud provider community but it looses focus very often. Nevertheless it tries to provide other side of story which no other book in market is providing.
Book consists of nine chapters which covers history of computers, various services offered by cloud, introduction to virtualization, standards in cloud, some talk about security and privacy in cloud, and accessing the cloud. Book also have two appendices which covers hands on Sun VirtualBox and case study on executive talk on cloud adoption.
Book provide lot of references which I like particularly. Book also scratches few of the topic which no other book has covered ( at least I have not encountered) like security and privacy in cloud in detail ( there is scope of much improvement), identity management in cloud ( again with huge scope of improvement) etc.
I suggest, read this book once but certainly it does not deserve to be in my bookshelf.
Disclaimer: I did not get paid to review this book, and I do not stand to gain anything if you buy the book. I have no relationship with the publisher or the author.
One can get more information about book and related topics from:
1. Amazon: http://www.amazon.com/Cloud-Computing-Implementation-Management-Security/dp/1439806802
2. Flipkart: http://www.flipkart.com/cloud-computing-john-rittinghouse-james-book-1439806802
3. Dr. John W. Rittinghouse resume: http://www.aphanes.net/JR%20Bio.html
Thursday, June 3, 2010
Categorization
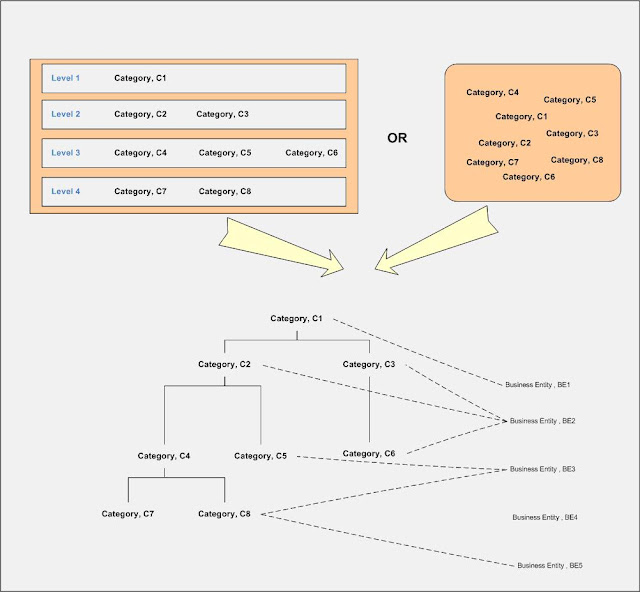
In any software system categorization of business entities is one of the most common features. During the course of creating product definition of one of the product under my portfolio, I again I encountered the dilemma of efficient categorization of business entities. To appreciate various categorization schemes available, I like to share with wider audiences and like to know are there any other possibilities exist.
Scheme 1: This is the traditional approach where categories and sub categories form a tree structure (each category as node) and business entities represent leaf under one node.
This scheme might have variation in terms of depth and breadth of tree, number of business entities per category and presence of single business entity under various categories.
Scheme 2: This is the approach where categories and sub category form a tree similar to Scheme1 but business entities do not become part of tree.
In this scheme, a business entity forms association with zero or more categories and similarly a category might be associated with one or business entities. In this scheme, depth and breadth of tree are mostly dependent upon business requirements similar to scheme 1. Applications might have one or more trees as per the business requirements.
Scheme 3: In this scheme, categories are formed as orphan entities in predefined level. Later these categories are associated to form tree similar to either to scheme 1 or scheme 2.
Option 1: Similar to Scheme 1
Option 2: Similar to Scheme 2
Scheme 4: This scheme categories form graph structure and then business entities are associated later to the graph node. This scheme is difficult to process due to inherent difficulty of graph structure.
Scheme 1: This is the traditional approach where categories and sub categories form a tree structure (each category as node) and business entities represent leaf under one node.
This scheme might have variation in terms of depth and breadth of tree, number of business entities per category and presence of single business entity under various categories.
Scheme 2: This is the approach where categories and sub category form a tree similar to Scheme1 but business entities do not become part of tree.
In this scheme, a business entity forms association with zero or more categories and similarly a category might be associated with one or business entities. In this scheme, depth and breadth of tree are mostly dependent upon business requirements similar to scheme 1. Applications might have one or more trees as per the business requirements.
Scheme 3: In this scheme, categories are formed as orphan entities in predefined level. Later these categories are associated to form tree similar to either to scheme 1 or scheme 2.
Option 1: Similar to Scheme 1
Option 2: Similar to Scheme 2
Scheme 4: This scheme categories form graph structure and then business entities are associated later to the graph node. This scheme is difficult to process due to inherent difficulty of graph structure.
Wednesday, June 2, 2010
Book Review: Cloud Computing: A Practical Approach
Book Review: Cloud Computing: A Practical Approach by Anthony T. Velte, Toby J. Velte, Robert Elsenpeter: Publisher- McGraw Hill: ISBN- 13: 978-0-07-162695-8
Cloud Computing: A Practical Approach is another me too book on cloud computing. Book tries to cover too many topics in too few pages.
Book consists of three parts: Getting Started – covers basics of cloud computing which in turn divided into four neat chapters. Second Part is Cloud Computing Technology – covers technical aspects at the cloud providers’ end and with little touch at consumer end as well. This part consists four chapters not so neatly separated. The third and last part is named as Cloud Computing at Work –covers some of the aspects of development of cloud based applications, migrating to them and associated subjects in six chapters.
Book is primarily focused on casual readers, so I don’t think it has any bookshelf value.
Disclaimer: I did not get paid to review this book, and I do not stand to gain anything if you buy the book. I have no relationship with the publisher or the author.
One can get more information about book and related topics from:
1. Publisher: http://www.mhprofessional.com/product.php?cat=112&isbn=0071626948
2. Flipkart: http://www.flipkart.com/book/cloud-computing-practical-approach-toby/0070683514
3. Amazon: http://www.amazon.com/Cloud-Computing-Practical-Approach-Velte/dp/0071626948
4. Review: http://iphonedevelopmenttextbooks.blogspot.com/2010/05/cloud-computing-practical-approach.html
5. Sony store: http://ebookstore.sony.com/ebook/toby-velte/cloud-computing-a-practical-approach/_/R-400000000000000178791
6. Good Reads: http://www.goodreads.com/book/show/7084900-cloud-computing-a-practical-approach
7. A1 Books: http://www.a1books.co.in/searchdetail.do?a1Code=booksgoogle&itemCode=0071626948
Cloud Computing: A Practical Approach is another me too book on cloud computing. Book tries to cover too many topics in too few pages.
Book consists of three parts: Getting Started – covers basics of cloud computing which in turn divided into four neat chapters. Second Part is Cloud Computing Technology – covers technical aspects at the cloud providers’ end and with little touch at consumer end as well. This part consists four chapters not so neatly separated. The third and last part is named as Cloud Computing at Work –covers some of the aspects of development of cloud based applications, migrating to them and associated subjects in six chapters.
Book is primarily focused on casual readers, so I don’t think it has any bookshelf value.
Disclaimer: I did not get paid to review this book, and I do not stand to gain anything if you buy the book. I have no relationship with the publisher or the author.
One can get more information about book and related topics from:
1. Publisher: http://www.mhprofessional.com/product.php?cat=112&isbn=0071626948
2. Flipkart: http://www.flipkart.com/book/cloud-computing-practical-approach-toby/0070683514
3. Amazon: http://www.amazon.com/Cloud-Computing-Practical-Approach-Velte/dp/0071626948
4. Review: http://iphonedevelopmenttextbooks.blogspot.com/2010/05/cloud-computing-practical-approach.html
5. Sony store: http://ebookstore.sony.com/ebook/toby-velte/cloud-computing-a-practical-approach/_/R-400000000000000178791
6. Good Reads: http://www.goodreads.com/book/show/7084900-cloud-computing-a-practical-approach
7. A1 Books: http://www.a1books.co.in/searchdetail.do?a1Code=booksgoogle&itemCode=0071626948
Tuesday, June 1, 2010
Top 11 Bad Performance Causes of Enterprise Scale applications
1. Database related challenges
a. Too much normalization
b. Not optimized queries
c. Excessive emphasis of keeping logic away from database engine
d. Improper indexing
e. Faulty installation of database server
2. Unnecessary remoting
a. Unnessary distribution of component across network
b. Too much emphasis on services
3. Faulty Deployment
a. Faulty deployment topology
b. Incorrect capacity planning
4. Faulty implementation of Concurrency
a. Long running methods are synchronized
b. Deadlock conditions are not envisioned
c. Long running data base transactions
5. Badly performing 3rd party libraries
a. Performance challenges in libraries
b. Bugs in libraries
6. Excessive usage of Hardware or software resources
a. Unnecessary IO operations
b. Incorrect usage of memory
7. Improper Caching
a. Not using caching
b. Not using proper caching platform
c. Not using features of caching platform
8. Excessive use XML
a. Obsessive use of XML
9. Incorrect usage of language features
a. exception as if condition
b. nested if conditions or for/while loops
c. faulty UI
d. IO operations, etc
10. Incorrect configuration of container
a. Application server
b. Virtual Machine
11. Excessive logging
a. Too much normalization
b. Not optimized queries
c. Excessive emphasis of keeping logic away from database engine
d. Improper indexing
e. Faulty installation of database server
2. Unnecessary remoting
a. Unnessary distribution of component across network
b. Too much emphasis on services
3. Faulty Deployment
a. Faulty deployment topology
b. Incorrect capacity planning
4. Faulty implementation of Concurrency
a. Long running methods are synchronized
b. Deadlock conditions are not envisioned
c. Long running data base transactions
5. Badly performing 3rd party libraries
a. Performance challenges in libraries
b. Bugs in libraries
6. Excessive usage of Hardware or software resources
a. Unnecessary IO operations
b. Incorrect usage of memory
7. Improper Caching
a. Not using caching
b. Not using proper caching platform
c. Not using features of caching platform
8. Excessive use XML
a. Obsessive use of XML
9. Incorrect usage of language features
a. exception as if condition
b. nested if conditions or for/while loops
c. faulty UI
d. IO operations, etc
10. Incorrect configuration of container
a. Application server
b. Virtual Machine
11. Excessive logging
Subscribe to:
Posts (Atom)